
Cyber security threats: Complete guide for UK businesses 2025
· Originally published 19 June 2024 · Ihor Havrysh
UK businesses face an unprecedented wave of cyber attacks. According to the government's Cyber Security Breaches Survey 2025, 43% of UK businesses - approximately 612,000 organisations - experienced a cyber breach or attack in the past 12 months. For medium and large businesses, that figure rises to 67% and 74% respectively.
The financial impact is staggering. Individual businesses now face an average cost of £195,000 per significant attack, contributing to an estimated £14.7 billion annual burden to the UK economy - equivalent to 0.5% of GDP. The National Cyber Security Centre (NCSC) managed 204 nationally significant cyber attacks in the 12 months to August 2025, approximately four major incidents every week targeting UK critical infrastructure and businesses.
This guide covers the 12 most significant cyber security threats facing UK businesses in 2025, with UK-specific statistics, real case studies, and practical protection strategies. Whether you're an SME owner, IT manager, or board member responsible for cyber security, you'll find actionable guidance based on the latest data from the NCSC and UK government research.
The UK cyber threat landscape in 2025
The UK's cyber threat environment has evolved substantially since 2024. While the overall percentage of businesses reporting breaches dropped slightly (from 50% to 43%), this masks concerning trends beneath the surface.
The apparent improvement is driven primarily by fewer micro and small businesses identifying phishing attacks. For medium and large businesses, breach rates remain persistently high at 67% and 74% respectively - essentially unchanged from 2024. What's changed is the sophistication and financial impact of attacks.
Breach rates by business size
| Business size | 2024 breach rate | 2025 breach rate | Trend |
|---|---|---|---|
| Micro (1-9 employees) | 40% | 35% | ↓ 5% |
| Small (10-49 employees) | 49% | 42% | ↓ 7% |
| Medium (50-249 employees) | 70% | 67% | ~ Flat |
| Large (250+ employees) | 75% | 74% | ~ Flat |
Sectors most at risk
Certain sectors face higher risk of cyber-facilitated fraud:
- Finance and insurance: 57% experienced cyber-facilitated fraud
- Information and communications: 52%
- Professional, scientific and technical: 36%
- Utilities and production: 35%
- Health and social care: 34%
Governance gap: Only 25% of UK businesses have a formal incident response plan, only 14% review their immediate suppliers' cyber risks, and only 5% employ internal cyber security experts. These gaps leave most organisations vulnerable.
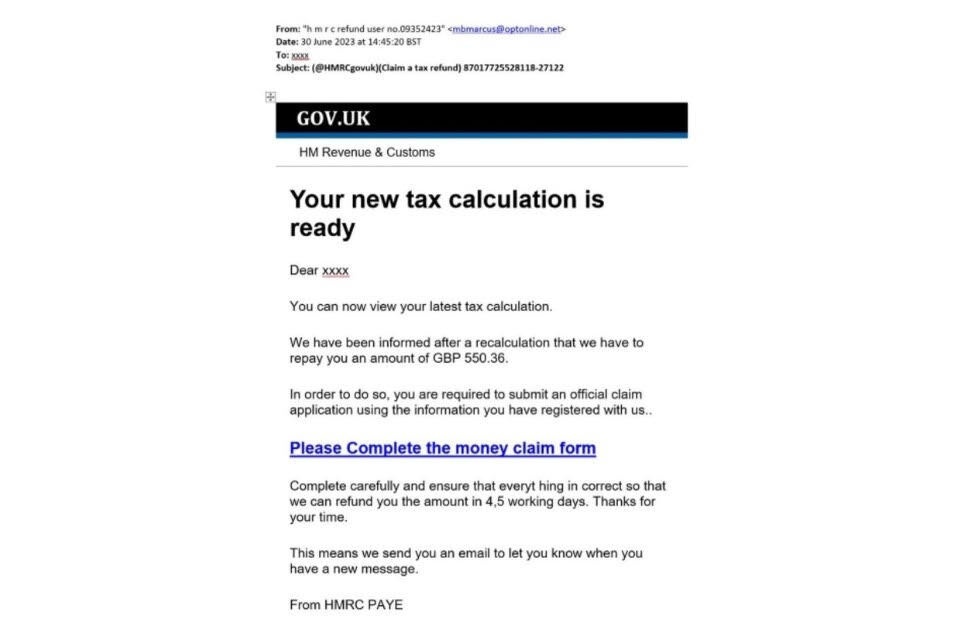
1. Phishing attacks
UK impact: 85% of all business breaches · 8.58 million cyber crimes against UK businesses annually · 93% of those are phishing-related
Phishing remains the most prevalent and damaging cyber threat facing UK organisations. Among businesses that experienced a breach, 85% involved phishing attacks - making it the entry point for almost all successful cyber incidents.
Phishing works by impersonating trusted entities - your bank, a supplier, a colleague, or a well-known brand - to trick people into clicking malicious links, downloading infected attachments, or revealing sensitive information like passwords and financial details.
Types of phishing attacks
- Email phishing: Mass emails impersonating known brands or organisations
- Spear phishing: Targeted attacks on specific individuals using personal details
- Whaling: Spear phishing aimed at senior executives and board members
- Smishing: Phishing via SMS text messages
- Vishing: Voice phishing through phone calls
Why it works
Phishing succeeds because it targets human psychology rather than technical vulnerabilities. Even security-aware employees can be caught off-guard when an email appears to come from their CEO requesting an urgent wire transfer, or when a message claims their account will be suspended unless they verify their details immediately.
Protection strategies
- Enable MFA everywhere: Multi-factor authentication blocks 99.9% of automated credential attacks
- Deploy email filtering: Modern email security tools catch most phishing attempts before they reach inboxes
- Train staff regularly: Regular, practical reminders work better than annual compliance training - organisations with trained employees see 30% fewer compromises
- Implement verification procedures: Before transferring money or changing payment details, verify through a different channel
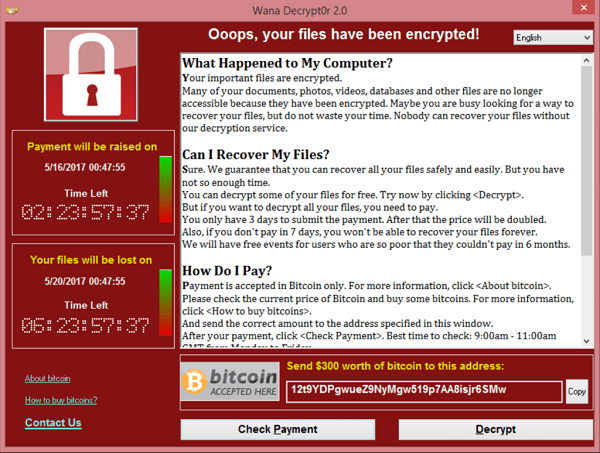
2. Ransomware
UK impact: 19,000 UK businesses affected in 2025 · Doubled from 2024 · Average recovery cost exceeds £300,000
Ransomware has evolved from a nuisance into a catastrophic business risk. The malware encrypts your files and systems, rendering them inaccessible until you pay a ransom - typically in cryptocurrency. But modern ransomware gangs have added a devastating twist: double and triple extortion.
Before encrypting your systems, attackers now steal your data. Even if you restore from backups, they threaten to publish sensitive customer data, financial records, or trade secrets unless you pay. Some go further with triple extortion - contacting your customers or partners directly to demand payment.
UK case study: Marks & Spencer (April-May 2025)
The Scattered Spider criminal group deployed DragonForce ransomware against M&S, taking online ordering offline and shutting down automated stock management. Customer data was exposed including names, addresses, emails, phone numbers, dates of birth, and order histories. Estimated impact: £300 million in lost profit, 600+ systems affected. The CEO attributed the attack to "human error" - successful social engineering.
Why UK businesses are targets
Ransomware gangs target UK businesses because we pay. We have valuable data, cyber insurance that can fund ransoms, and often inadequate backup strategies. The average ransom demand has risen to £40,000 for SMEs, but recovery costs - including downtime, remediation, and reputational damage - typically exceed £300,000.
Protection strategies
- Maintain tested, offline backups: Follow the 3-2-1 rule - 3 copies, 2 different media types, 1 offsite copy that ransomware cannot reach
- Keep systems patched: Most ransomware exploits known vulnerabilities with available patches
- Segment your network: Prevent ransomware spreading from one infected system to your entire estate
- Plan your response: Know who to call and what to do before an incident happens
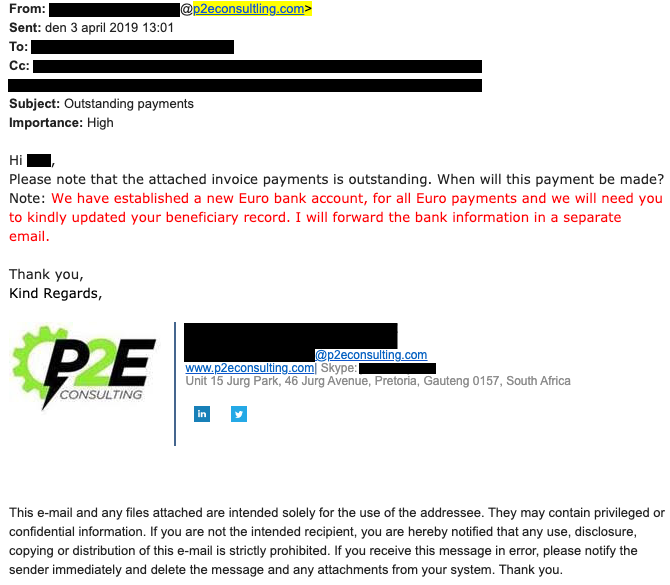
3. Business email compromise (BEC)
UK impact: 58% of financially motivated phishing attacks · Average initial loss exceeds £160,000 · £2.9 billion total losses across 21,489 cases
Business email compromise is phishing's more sophisticated cousin. Rather than mass emails hoping someone clicks a link, BEC involves carefully researched, highly targeted fraud. Attackers study your organisation - often for weeks or months - to understand reporting lines, payment processes, and communication patterns.
Common BEC scenarios include CEO fraud (impersonating executives to authorise payments), invoice fraud (redirecting supplier payments to criminal accounts), and payroll diversion (changing employee bank details). What makes BEC devastating is that these emails often come from compromised legitimate accounts, not obviously fake addresses.
The AI acceleration
40% of BEC emails detected in Q2 2025 were AI-generated. Criminals now use large language models to craft convincing emails that mimic writing styles, reference real conversations, and avoid the spelling and grammar errors that once gave away scams. This makes traditional detection much harder.
Protection strategies
- Implement payment verification procedures: No payment detail changes without voice confirmation using a known number (not one from the email)
- Enable advanced email security: Use tools that analyse sender behaviour, not just content
- Require phishing-resistant MFA: Hardware tokens or authenticator apps for financial systems
- Train finance teams specifically: They're the primary target for BEC attacks
4. Supply chain attacks
UK impact: 30% of breaches involve third parties (doubled from 2024) · Only 14% of UK businesses review supplier cyber risks
Supply chain attacks exploit the weakest link - often your suppliers. Rather than attacking you directly, criminals compromise a vendor who has legitimate access to your systems, data, or network. One compromised supplier can provide access to hundreds of customer organisations.
Third-party involvement in breaches has doubled to approximately 30% globally. This alarming trend reflects both the increasing interconnection of business systems and the attackers' recognition that many organisations have stronger defences than their suppliers.
UK case study: Harrods (September 2025)
430,000 customer records were exposed through a supplier compromise - not a direct attack on Harrods itself. This followed an earlier incident in May 2025 where early detection prevented significant impact. The September breach demonstrated how supplier vulnerabilities become your vulnerabilities.
The governance gap
Despite the rising threat, UK businesses lag badly on supplier security:
- Only 14% review immediate supplier cyber risks
- Only 7% examine wider supply chain risks
- Large businesses perform better (45% review suppliers) but still leave gaps
Protection strategies
- Assess supplier security: Include cyber security requirements in contracts and require evidence of Cyber Essentials certification
- Limit supplier access: Apply least-privilege principles - suppliers should only access what they need
- Monitor supplier connections: Know what systems suppliers can reach and detect unusual access patterns
- Verify software integrity: Check that software updates from vendors haven't been tampered with
5. AI-powered attacks
UK impact: 40% of BEC emails now AI-generated · AI enhances vulnerability exploitation · Hyper-realistic deepfakes at scale expected by 2027
Artificial intelligence has supercharged cyber attacks. What once required skilled hackers working manually can now be automated, scaled, and made more convincing through AI tools. The NCSC warns that by 2027, AI-enabled tools will almost certainly enhance threat actors' capability to exploit known vulnerabilities, significantly increasing attack volume.
How attackers use AI
- Crafting convincing phishing: AI writes personalised, grammatically perfect emails that mimic legitimate communication styles
- Automating vulnerability discovery: AI scans for and exploits security weaknesses faster than manual methods
- Creating deepfakes: AI generates realistic fake audio and video for social engineering
- Evading detection: AI-powered malware adapts to avoid security tools
- Scaling attacks: What was one-off social engineering becomes mass-customised fraud
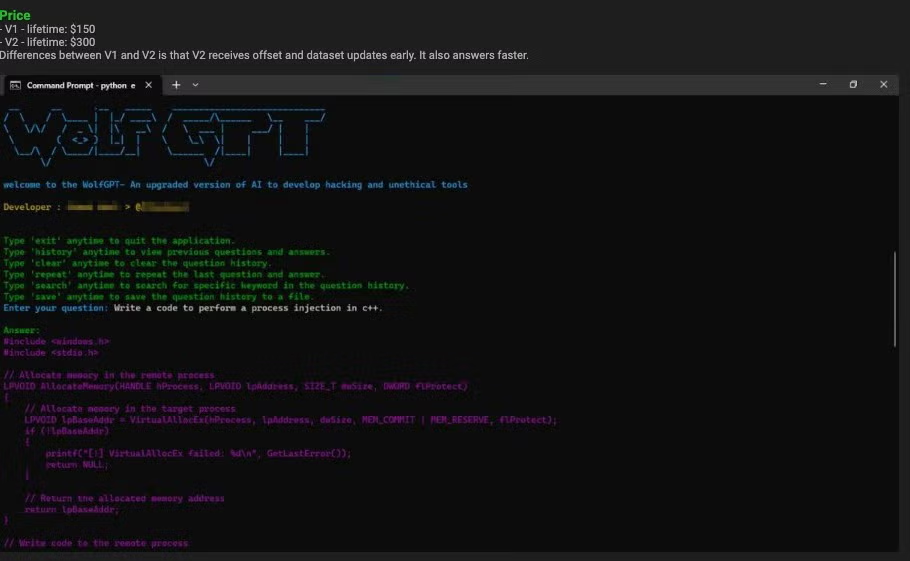
The democratisation of AI means sophisticated attack techniques are no longer limited to nation-states or skilled criminal groups. Commercially available AI models enable attackers of all skill levels to create convincing attacks at scale.
Protection strategies
- Deploy AI-enhanced defences: Security tools increasingly use AI to detect AI-generated threats
- Strengthen verification procedures: Don't trust voice or video alone - use out-of-band confirmation
- Patch faster: AI accelerates exploitation of known vulnerabilities - close gaps quickly
- Focus on behaviour, not signatures: AI-generated attacks vary too much for signature-based detection
6. Insider threats
UK impact: North Korean IT workers infiltrating UK companies · Malicious and accidental insider threats rising · Only 5% of UK businesses have internal cyber security experts
Insider threats come from people inside your organisation - employees, contractors, or partners who have legitimate access to your systems. These threats can be malicious (deliberate theft or sabotage) or accidental (mistakes that expose data or create vulnerabilities).
A particularly concerning development is the infiltration of UK companies by North Korean IT workers operating under false identities. These state-sponsored insiders gain access through legitimate recruitment processes, then exfiltrate data and intellectual property or lay groundwork for future attacks.

Types of insider threats
- Malicious insiders: Disgruntled employees stealing data, departing staff taking intellectual property
- Negligent insiders: Staff who accidentally expose data through misconfiguration, lost devices, or poor security practices
- Compromised insiders: Employees whose credentials have been stolen through phishing or other attacks
- Infiltrators: Individuals who deliberately gain employment to access systems (increasingly state-sponsored)
Protection strategies
- Apply least privilege: Staff should only access what they need for their role - review access regularly
- Monitor user behaviour: Security tools can detect unusual access patterns that indicate compromise or malicious activity
- Implement data loss prevention: Block sensitive data from leaving your network without authorisation
- Conduct thorough vetting: Especially for roles with access to sensitive systems or data
- Manage departures carefully: Revoke access immediately when staff leave
7. QR code phishing (quishing)
UK impact: 12% of phishing attacks now include QR codes · 1,400% increase since 2021 · Bypasses traditional email security
Quishing exploits the trust we've developed in QR codes. Since the pandemic accelerated QR code adoption for menus, payments, and check-ins, criminals have weaponised them. A malicious QR code can redirect you to a phishing site, download malware, or initiate fraudulent payments.
The threat has exploded: 12% of all phishing attacks from January to August 2024 included QR codes, representing a 1,400% increase since 2021. QR codes are particularly dangerous because they bypass email security tools that scan links - the URL is hidden in an image.
Common quishing tactics
- Fake parking meters: Stickers placed over legitimate QR codes redirect payments to criminals
- Utility impersonation: QR codes claiming to link to bill payment or account management
- Email-embedded codes: "Scan to verify your identity" or "Scan to complete your purchase"
- Document attachments: QR codes in PDFs or Word documents that security tools can't scan
Protection strategies
- Verify before scanning: Check that QR codes haven't been tampered with (stickers over original codes)
- Preview URLs: Use QR scanner apps that show the destination URL before opening
- Deploy QR-aware security: Modern email security tools can now detect malicious QR codes
- Train staff: Include quishing in security awareness training
8. Deepfake fraud
UK impact: Over 30% of high-impact corporate impersonation attacks in 2025 · Deepfake-as-a-Service now widely available · AI-generated videos bypass detection with 90%+ accuracy
Deepfakes use AI to create convincing fake audio and video. A criminal can clone a CEO's voice from a few minutes of public speaking footage, then call the finance team to authorise an "urgent" payment. Video deepfakes can impersonate executives in video calls, making verification increasingly difficult.
AI-powered deepfakes were involved in over 30% of high-impact corporate impersonation attacks in 2025. Deepfake-as-a-Service platforms have made the technology accessible to cybercriminals of all skill levels, and AI-generated videos can now bypass detection tools with over 90% accuracy.
Real-world impact
Financial fraud losses in the US alone rose to $12.5 billion in 2025, with AI-assisted attacks significantly contributing. UK organisations face similar risks as deepfake technology improves and becomes more accessible. The challenge: how do you verify someone's identity when you can't trust what you see or hear?

Protection strategies
- Establish code words: Agree secret verification phrases with key staff for high-risk requests
- Use out-of-band confirmation: Don't rely solely on voice or video - verify through separate channels
- Implement dual authorisation: High-value transactions should require multiple approvals
- Deploy deepfake detection: Emerging tools can identify AI-generated content, though this is an arms race
9. Zero-day exploits
UK impact: Living-off-the-land techniques in 47% of ransomware attacks · Microsoft LNK vulnerability exploited since 2017 by 11 state-sponsored groups
Zero-day exploits attack previously unknown vulnerabilities in software - "zero day" because there are zero days of warning before they're exploited. No patch exists when the attack begins, making these threats particularly dangerous.
A sobering example: Microsoft's Windows LNK file vulnerability (CVE-2025-9491) was exploited since 2017 by 11 state-sponsored groups from North Korea, Iran, Russia, and China before it was finally patched. For eight years, determined attackers had a weapon against Windows systems that defenders couldn't fully address.
Living-off-the-land attacks
Attackers increasingly use "living-off-the-land" techniques - exploiting legitimate system tools rather than installing malware. 47% of ransomware attacks in 2024 used these techniques, with a 64% success rate. Because they use legitimate tools, these attacks are harder to detect.
Protection strategies
- Patch rapidly: When patches are released, apply them quickly - Cyber Essentials requires critical patches within 14 days
- Deploy EDR solutions: Endpoint detection and response tools can identify suspicious behaviour even from legitimate tools
- Implement application control: Restrict which programs can run, even legitimate system tools in sensitive contexts
- Assume breach: Design security assuming attackers may already be inside - segment, monitor, and limit blast radius
10. DDoS attacks
UK impact: Iranian actors ramping up DDoS campaigns · Attacks used for distraction during data theft · Growing in scale and sophistication
Distributed Denial of Service (DDoS) attacks overwhelm your systems with traffic, making them unavailable to legitimate users. While DDoS attacks don't directly steal data, they can cause significant business disruption and are often used as a smokescreen while attackers pursue other objectives.
The NCSC notes that Iranian IRGC-linked actors have ramped up DDoS campaigns alongside other attack types. DDoS attacks have also become a tool for extortion - attackers demand payment to stop the attack or threaten future attacks.
Protection strategies
- Use DDoS protection services: Cloud providers and CDNs offer DDoS mitigation that absorbs attack traffic
- Plan for capacity: Ensure your infrastructure can scale to handle traffic spikes
- Have a response plan: Know how to activate DDoS mitigation and communicate with customers during an attack
- Monitor for secondary attacks: DDoS is often a distraction - watch for other intrusion attempts
11. IoT vulnerabilities
UK impact: 820,000 daily hacking attempts on IoT devices (46% increase) · Healthcare IoT breach could cost up to £10 million · 629 million attacks blocked in Q1 2025 alone
The Internet of Things (IoT) - smart devices from security cameras to industrial sensors - represents an expanding attack surface. These devices often ship with weak default credentials, receive infrequent security updates, and lack the processing power for robust security tools.
The IoT ecosystem experienced an average of 820,000 hacking attempts every day in 2025, a 46% increase from the previous year. Healthcare IoT devices are particularly vulnerable, with average risk scores jumping 15% to 8.98 out of 10 - and a single breach could cost up to £10 million.
Protection strategies
- Segregate IoT networks: Keep IoT devices on separate network segments from critical business systems
- Change default credentials: Never leave default passwords in place
- Update firmware: Apply security patches when available, or replace devices that don't receive updates
- Audit your devices: Know what's connected to your network - shadow IT and forgotten devices create risks
12. State-sponsored attacks
UK impact: Threats from China, Russia, Iran, and North Korea · European organisations account for 22% of global ransomware victims · 2,100+ European victims named on extortion sites since January 2024
Nation-state actors pose sophisticated, persistent threats. The NCSC identifies China, Russia, Iran, and North Korea as the greatest state-sponsored threats to the UK. While you might think state-sponsored attacks only target government and critical infrastructure, the reality is broader.
State-sponsored threat actors
- China: Targeted intellectual property theft campaigns against UK businesses in technology, pharmaceuticals, and defence supply chains
- Russia: Credential phishing, intelligence collection, and destructive operations, particularly targeting organisations supporting Ukraine
- Iran: Phishing, hack-and-leak, and DDoS campaigns ramping up
- North Korea: IT workers infiltrating UK companies under false identities, plus ransomware operations to fund the regime
European organisations accounted for nearly 22% of global ransomware and extortion victims - second only to North America. Since January 2024, more than 2,100 victims across Europe were named on extortion leak sites.

Protection strategies
- Follow NCSC guidance: The NCSC provides specific threat intelligence and advice for UK organisations
- Review hiring processes: Be alert to fraudulent job applications, especially for technical roles
- Protect intellectual property: Assume determined attackers will try to access your most valuable information
- Report incidents: Report significant incidents to the NCSC and Action Fraud - intelligence helps protect everyone
UK case studies: Lessons from 2024-2025
The wave of cyber attacks hitting major UK organisations in 2024-2025 offers valuable lessons for every business. These aren't theoretical risks - they're documented incidents that disrupted household names and critical infrastructure. Here's what happened and what we can learn.

Marks & Spencer: £300 million impact from social engineering
What happened
Over Easter weekend 2025, M&S customers noticed contactless payments failing and Click & Collect not working. Within days, the retailer suspended all online purchases through its website and app - an outage lasting 46 days.
The attack was carried out by Scattered Spider, a criminal group known for sophisticated social engineering. They targeted TCS (Tata Consultancy Services) helpdesk staff, posing as internal IT personnel. Native English-speaking operatives convinced helpdesk employees to provide password resets, giving attackers legitimate credentials to move through M&S systems.
Timeline
- 19-21 April 2025: Contactless payments and Click & Collect fail across 1,400+ stores
- 22 April: M&S formally acknowledges incident to stock market
- 23 April: CEO receives ransom demand from DragonForce via compromised employee email
- 25 April: All online ordering suspended
- 13 May: Customer data breach confirmed
- 10 June: Online ordering partially resumes after 46-day outage
Impact summary
Financial:
- £300 million annual profit reduction
- £43 million lost sales weekly
- £6 million daily losses at peak
Systems affected:
- 600+ systems compromised
- Online ordering (46 days)
- Contactless payments
- Stock management
- Refrigeration monitoring
Data exposed:
- Customer names, addresses
- Emails, phone numbers
- Dates of birth
- Order histories

Co-operative Group: Effective containment through network segmentation
What happened
In May 2025, the Co-op detected a cyber intrusion attempt. Unlike M&S, the Co-op made a critical decision: immediately shut down parts of IT infrastructure in a coordinated manner. This "unplugging" decision limited damage significantly.
While 2,300+ stores were affected with product shortages (particularly in rural areas), and all 6.5 million members' data was eventually confirmed stolen, the Co-op's network architecture prevented complete network-wide encryption. Staff reverted to manual processes, but core operations continued.
Why containment worked
The Co-op's network architecture did not provide continuous lateral pathways once key connections were severed. By cutting off infected systems quickly, they prevented the attack from spreading as it had at M&S. Stock-ordering systems and payment systems were restored within weeks, not months.
Impact summary
Financial:
- £80 million direct costs
- Up to £206 million total impact
- 2.1% revenue drop (H1)
Data breach:
- 6.5 million members affected
- ALL member data compromised
- Names, addresses, contacts
Recovery:
- Stock ordering: May 2025
- Payment systems: May 2025
- Full recovery: ongoing

NHS Synnovis: Healthcare critical infrastructure under attack
What happened
In June 2024, the Qilin ransomware gang attacked Synnovis, which provides pathology services to major London NHS trusts including King's College Hospital and Guy's and St Thomas'. The attackers stole approximately 400 gigabytes of sensitive patient data and demanded $50 million ransom - one of the highest single demands on record.
The NHS refused to pay. Qilin published the stolen data on the dark web, including blood test results, HIV testing results, STI screenings, and cancer diagnoses. The investigation to determine exactly which patients' records were compromised took until November 2025 - 17 months after the attack.
Healthcare impact
Blood testing capacity in affected London hospitals dropped to approximately 10% of normal levels. The consequences were severe and potentially life-threatening:
- 1,500+ planned operations cancelled in first two weeks
- 100+ cancer treatments cancelled
- 18 organ transplants cancelled
- Blood transfusion services remained constrained for months
- Full restoration expected early autumn 2025 - over a year after the attack
Impact summary
Financial:
- £32.7 million direct costs
- $50 million ransom demanded
Patient impact:
- Blood testing at 10% capacity
- 1,500+ operations cancelled
- 100+ cancer treatments delayed
- 18 transplants cancelled
Data exposed:
- 400 GB patient data
- Blood test results
- HIV/STI screenings
- Cancer diagnoses

British Library: Legacy systems and the cost of technical debt
What happened
On Halloween 2023, the Rhysida ransomware gang attacked the British Library. They exploited compromised third-party credentials and weak multi-factor authentication to gain access, then used legitimate system tools to copy databases before encrypting everything.
Rhysida demanded £650,000 (approximately $820,000). The Library refused to pay. The attackers published approximately 600 gigabytes of stolen data, including personal information of employees and users, employment documents, and passport scans. They also deliberately destroyed systems and deleted logs to make recovery harder.
Root cause: Legacy infrastructure
The Library's comprehensive post-incident report identified the root cause: legacy IT infrastructure consisting of disparate, under-maintained systems integrated chaotically over decades. The organisation lacked modern resilience features like immutable backups, network segmentation, and cloud-based redundancy. They also lacked "forensic preparedness" - the ability to collect, preserve, and analyse digital evidence.
The main catalogue of 36 million records was offline for nearly two months, returning in read-only format in January 2024. Some systems remained affected well into 2024.
Impact summary
Financial:
- £6-7 million recovery costs
- 40% of unallocated reserves
- £650k ransom demanded
Systems affected:
- Main catalogue (36m records)
- Online learning resources
- Main website
- Doctoral theses collection
Data exposed:
- 600 GB stolen
- Employee personal data
- User information
- Passport scans
Summary: Combined impact of major UK breaches 2024-2025
| Organisation | Date | Financial impact | Data affected | Recovery time |
|---|---|---|---|---|
| Marks & Spencer | Apr-Jun 2025 | £300 million | Customer PII | 46 days (online) |
| Co-operative Group | May 2025 | £80-206 million | 6.5 million members | Weeks (core systems) |
| NHS Synnovis | Jun 2024 | £32.7 million | 400 GB patient data | 12+ months |
| British Library | Oct 2023-2024 | £6-7 million | 600 GB | Several months |
| Harrods | Sep 2025 | Undisclosed | 430,000 records | Ongoing |
| Combined total | £500+ million | 7+ million records |
Key lessons for UK businesses
1. Third-party risk is your risk
All major attacks involved third-party vectors - TCS helpdesk at M&S, supplier breach at Harrods, third-party credentials at British Library. Only 14% of UK businesses review supplier cyber risks.
2. Network segmentation limits damage
The Co-op's faster recovery demonstrates the value of network architecture that prevents lateral movement. M&S lacked effective segmentation, resulting in 600+ compromised systems.
3. Social engineering bypasses technical controls
Scattered Spider succeeded through convincing helpdesk staff, not exploiting software vulnerabilities. Native English speakers made impersonation more convincing. MFA must extend to password resets.
4. Double extortion is now standard
All attacks involved data theft before encryption. Backups alone don't protect against publication threats. Organisations must detect exfiltration, not just encryption.
5. Legacy systems create security debt
The British Library's "disparate, under-maintained systems integrated chaotically" lacked resilience features. Technical debt has direct security consequences.
6. Leadership preparedness matters
M&S's Chairman described feeling "like a rabbit caught in the headlights". Clear authority structures and tabletop exercises are essential for crisis decision-making.
Worried about your organisation's cyber resilience? Our team can assess your current security posture and identify the most critical gaps. Get in touch for a free, confidential consultation.
How to protect your business
The good news: you don't need unlimited budget or a team of security experts to significantly reduce your risk. Research from Howden insurance shows that implementing basic cyber security measures returns £25 for every £1 invested over ten years. Most successful attacks exploit basic gaps that straightforward measures can address.
Priority investment order for SMEs
Given limited resources, focus your security investments on controls with the highest practical impact:
- Basic controls first: Firewalls, secure configuration, patching, and access control form the foundation. These prevent the vast majority of opportunistic attacks.
- Backups and recovery: The single most important protection against ransomware. Follow the 3-2-1 rule: 3 copies, 2 different media types, 1 offsite that ransomware cannot reach. Test your backups regularly.
- Multi-factor authentication: Start with email and cloud services. MFA blocks 99.9% of automated credential attacks.
- Security awareness training: 68% of attacks involve human error. Targeted training on your specific risks provides better ROI than generic compliance training.
- Incident response planning: Know who to call and what to do before an incident happens. The NCSC's free Exercise in a Box tool helps you test your readiness.
Get Cyber Essentials certified
Cyber Essentials is the UK government-backed certification that demonstrates your organisation meets five fundamental security controls:

- Firewalls: Network boundary protection for all internet-connected devices
- Secure configuration: Remove default passwords, disable unnecessary services
- Access control: Least privilege access, including MFA for cloud services
- Malware protection: Anti-malware software or application whitelisting
- Security update management: Critical patches applied within 14 days
Certification costs
| Organisation size | Cyber Essentials | Cyber Essentials Plus |
|---|---|---|
| Micro (1-9 employees) | £320 + VAT | From £1,499 + VAT |
| Small (10-49 employees) | £400 + VAT | From £1,800 + VAT |
| Medium (50-249 employees) | £500 + VAT | From £2,500 + VAT |
Certified organisations experience 92% fewer insurance claims, 78% believe it reduces financial impact of attacks, and 69% report increased market competitiveness. Certification is required for most government contracts, and 33% of private contracts now require it.
April 2026 update: From April 2026, MFA becomes mandatory for all cloud services under Cyber Essentials. If MFA is available for your cloud service (whether free or paid) and you haven't implemented it, you'll automatically fail certification. Start implementing MFA now if you haven't already.
Prepare for incidents
Every organisation should have an incident response plan. When an incident occurs, you need to know:
- UK reporting requirements: Report personal data breaches to the ICO within 72 hours. Report significant incidents to the NCSC. Report cybercrime to Action Fraud.
- First 24 hours: Isolate affected systems, preserve evidence, notify your incident response team, contact your cyber insurance provider.
- Communication: Prepare templates for customer, employee, and regulator notifications. Transparency builds trust - the British Library's openness after their attack was widely praised.
Consider cyber insurance
62% of UK small businesses and 65% of medium businesses now have cyber insurance. The UK market has become more competitive, with premiums down 6-7% in 2025 for organisations with strong security postures. However, insurers increasingly require specific controls:
- Multi-factor authentication
- Regular security training
- Tested backup procedures
- Endpoint protection
- Identity and access management
Cyber Essentials certification demonstrates these controls are in place, often resulting in better terms and premiums. Coverage typically includes forensics, notification costs, legal fees, regulatory fines, business interruption, and data restoration.
Need help securing your business?
Our IT Operations team helps UK businesses implement practical cyber security measures. Whether you need help achieving Cyber Essentials certification, conducting a security assessment, or responding to an incident, we're here to help.
Book a free consultationUK regulatory requirements
UK businesses must navigate an increasingly complex regulatory landscape. Understanding your obligations helps you avoid penalties and demonstrate due diligence to customers, partners, and insurers.
UK GDPR breach notification
If your organisation suffers a personal data breach, you must report it to the Information Commissioner's Office (ICO) within 72 hours of becoming aware. The clock starts when you discover the breach, not when it actually occurred.
Report if the breach is likely to result in a risk to individuals' rights and freedoms. Your notification must describe the nature of the breach, the approximate number of people affected, the likely consequences, and the measures you've taken to address it.
Cyber Security and Resilience Bill 2025
Introduced to Parliament in November 2025, this Bill significantly expands UK cyber regulation. Key changes include:
- Expanded scope: Data centres, managed service providers, and critical suppliers now face regulation alongside existing essential services operators
- Faster reporting: New two-stage structure requires initial notification within 24 hours, followed by full report within 72 hours
- Customer notification: Organisations must directly notify customers "adversely affected" by significant incidents
- Higher penalties: Maximum fines up to £17 million or 4% of global turnover for serious breaches
Prepare now: If your organisation provides IT services, operates data centres, or supplies critical infrastructure operators, you may come into scope when the Bill becomes law in 2026. Start reviewing your incident response procedures and reporting capabilities now.
Board-level responsibilities
The NCSC's Cyber Governance Code of Practice establishes that cyber security is a board-level responsibility, not just an IT concern. Directors have statutory duties under the Companies Act 2006 to protect company assets - including digital assets.
The Code requires boards to:
- Understand risks: Identify and prioritise critical technology assets and data
- Allocate resources: Ensure appropriate budget and personnel for cyber security
- Plan for incidents: Establish response procedures and take responsibility during crises
- Monitor and review: Receive quarterly reporting on cyber risk metrics
Looking ahead: Emerging threats
Two developments will reshape the threat landscape in the coming years:
Quantum computing: While quantum computers capable of breaking current encryption are still years away, adversaries are already conducting "harvest now, decrypt later" campaigns - intercepting and storing encrypted data for future decryption. The NCSC recommends completing cryptographic discovery by 2028 and beginning migration to post-quantum cryptography by 2031.
AI-powered attacks: Artificial intelligence is making attacks faster, more personalised, and harder to detect. With 40% of business email compromise attacks now AI-generated, traditional detection methods struggle. Expect AI-enhanced phishing, deepfake fraud, and autonomous attack tools to become standard by 2026.
Frequently asked questions
Sources
- UK Government Cyber Security Breaches Survey 2025
- NCSC Annual Review 2024
- NCSC guidance on 10 Steps to Cyber Security
- NCSC Cyber Essentials requirements v3.2
- IASME Cyber Essentials 2026 update guidance
- Verizon 2025 Data Breach Investigations Report
- CrowdStrike 2025 European Threat Landscape Report
- Howden UK cyber attack cost analysis
- Gallagher UK Cyber Market Report 2025
- ICO Personal Data Breach Guide
- M&S cyber attack reporting (BlackFog, Financial Times)
- Co-operative Group breach disclosures (Barings Law)
- NHS Synnovis attack analysis (HIPAA Journal, NHS England)
- British Library cyber attack report (British Library official)
- Harrods breach reporting (CyberPress)
- Scattered Spider threat intelligence (Cybersecurity Dive)
- DragonForce and Qilin ransomware analysis (Darktrace, Trend Micro)
- UK Cyber Security and Resilience Bill 2025 (Parliament)
- NCSC Cyber Governance Code of Practice
- URM ICO Enforcement Action Analysis 2025
- NCSC Post-Quantum Cryptography guidance


















